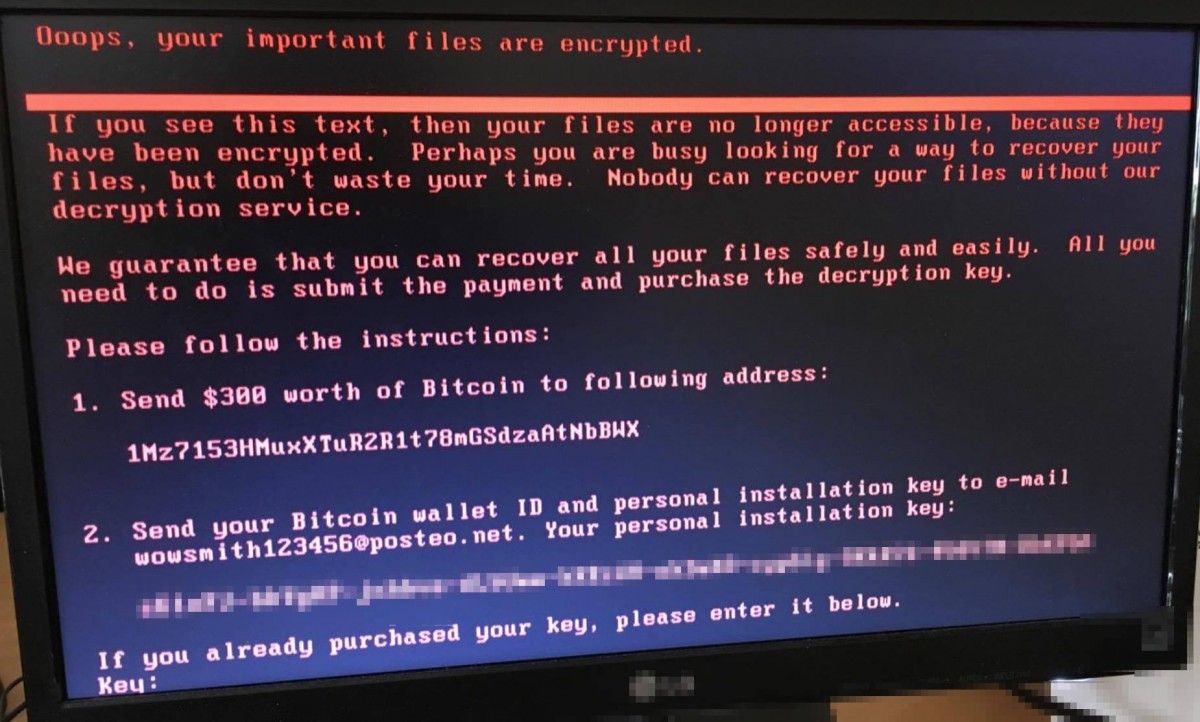
On June 27, 2017, a cyber attack hit many computer systems in Ukraine, as well as in other countries. That attack was spearheaded by the malware ESET products detect as Diskcoder.C (aka ExPetr, PetrWrap, Petya, or NotPetya). This malware masquerades as typical ransomware: it encrypts the data on the computer and demands $300 bitcoins for recovery. In fact, the malware authors' intention was to cause damage, so they did all that they could to make data decryption very unlikely, the report said.
The Cyberpolice Department of Ukraine's National Police stated, on its Facebook account, as did ESET and other information security companies, that the legitimate Ukrainian accounting software M.E.Doc was used by the attackers to push DiskCoder.C malware in the initial phase of the attack. However, until now, no details were provided as to exactly how it was accomplished.
The research identified a very stealthy and cunning backdoor that was injected by attackers into one of M.E.Doc's legitimate modules. It seems very unlikely that attackers could do this without access to M.E.Doc's source code.
Read alsoUkrainian cyberpolice seize server of small company linked to global attack – mediaThe backdoored module has the filename ZvitPublishedObjects.dll. This was written using the .NET Framework. It is a 5MB file and contains a lot of legitimate code that can be called by other components, including the main M.E.Doc executable ezvit.exe.
All M.E.Doc updates that were released during 2017 have been examined and it was found that there are at least three updates that contained the backdoored module: 01.175-10.01.176, released on April 14, 2017; 01.180-10.01.181, released on May 15, 2017; 01.188-10.01.189, released on June 22, 2017.
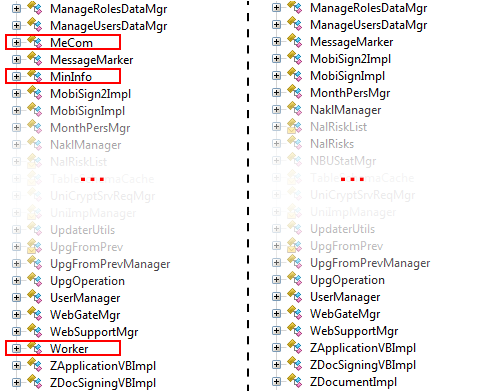
The main backdoor class is named MeCom and it is located in the ZvitPublishedObjects.Server namespace.
The methods of the MeCom class are invoked by the IsNewUpdate method of UpdaterUtils in the ZvitPublishedObjects.Server namespace. The IsNewUpdate method is called periodically in order to check whether a new update is available. The backdoored module from May 15 is implemented in a slightly different way and has fewer features than the one from June 22.
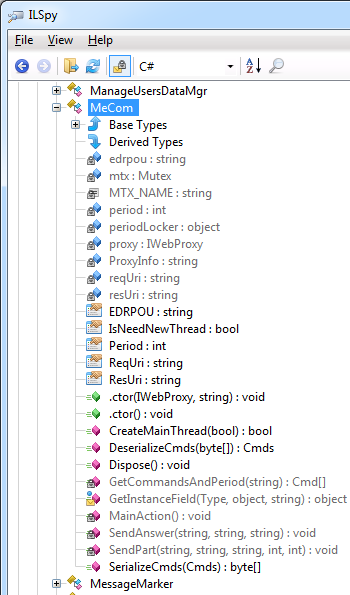
Each organization that does business in Ukraine has a unique legal entity identifier called the EDRPOU number (Код ЄДРПОУ). This is extremely important for the attackers: having the EDRPOU number, they could identify the exact organization that is now using the backdoored M.E.Doc. Once such an organization is identified, attackers could then use various tactics against the computer network of the organization, depending on the attackers' goal(s).
Since M.E.Doc is accounting software commonly used in Ukraine, the EDRPOU values could be expected to be found in application data on machines using this software. Hence, the code that was injected in the IsNewUpdate method collects all EDRPOU values from application data: one M.E.Doc instance could be used to perform accounting operations for multiple organizations, so the backdoored code collects all possible EDRPOU numbers.
Along with the EDRPOU numbers, the backdoor collects proxy and email settings, including usernames and passwords, from the M.E.Doc application.
The malicious code writes the information collected into the Windows registry under the HKEY_CURRENT_USER\SOFTWARE\WC key using Cred and Prx value names. So if these values exist on a computer, it is highly likely that the backdoored module did, in fact, run on that computer.
And here is the most cunning part! The backdoored module does not use any external servers as C&Cs: it uses the M.E.Doc software's regular update check requests to the official M.E.Doc server upd.me-doc.com[.]ua. The only difference from a legitimate request is that the backdoored code sends the collected information in cookies.
"As our analysis shows, this is a thoroughly well-planned and well-executed operation. We assume that the attackers had access to the M.E.Doc application source code. They had time to learn the code and incorporate a very stealthy and cunning backdoor. The size of the full M.E.Doc installation is about 1.5GB, and we have no way at this time to verify that there are no other injected backdoors," the authors of the analysis said.
They also recommend changing passwords for proxies, and for email accounts for all users of M.E.Doc software.

