As reported, a FireEye official said that the initial analysis of the EternalPetya virus found a lot in common with earlier cyberattacks carried out by Sandworm Team, which targeted Ukraine in December 2015, inflicting major losses to the country's energy companies. Although the analysts was not absolutely sure that the group was funded by the state, its goals are consistent with those of the Russian government.
According to the cyber police, its experts together with FireEye are conducting forensic surveys and studies of the affected servers and workstations. They are searching for factual evidence that will allow confirming the original vector of infection, identify personal computers that distributed malicious software, and recreate the chronology of events. In addition, FireEye specialists are studying the network equipment telemetry data to prevent similar attacks in the future.
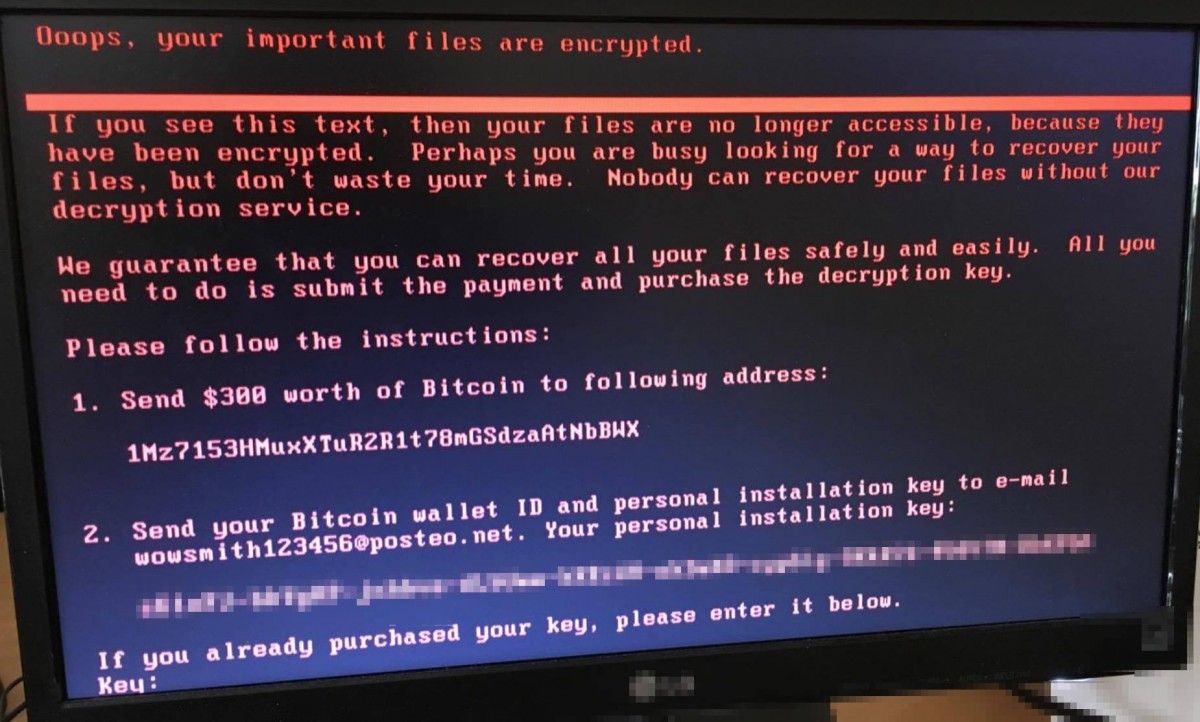
Read alsoUkraine "playground" for Russian cyberattacks - mediaAs UNIAN reported earlier, on June 27, Ukrainian banks, energy companies, state-owned Internet resources and local networks, as well as Ukrainian media suffered a mass cyberattack, which blocked the operation of computer networks.
In late December 2015, the Ukrainian enterprise Prykarpattyaoblenergo reported a cyberattack on its network. As a result, about 700,000 residents of Ivano-Frankivsk region were left without electricity.
Moreover, Kyivoblenergo, Chernivtsioblenergo, Khmelnitskoblenergo and Kharkivoblenergo have suffered cyberattacks as well, according to the State Special Communications Service of Ukraine.
Read alsoSBU: Ransom demands in cyberattack "only cover-up"The U.S.-based iSight Partners, specializing in cyber intelligence, claimed that Russia's Sandworm hacker group was involved in the power outage. It was reported earlier that the U.S. Central Intelligence Agency, the National Security Agency and the Department of Homeland Security intended to conduct an investigation into the involvement of Russian hackers in cyberattacks.

