
The SBU Security Service's counterintelligence department has successfully completed a sting operation to expose a network of Russian assets recruited by the FSB from among former officers with the spec-ops forces.
The group had been plotting subversive actions and abduction of a former chief of the Special Operations Forces, according to Liga.net citing the SBU press service.
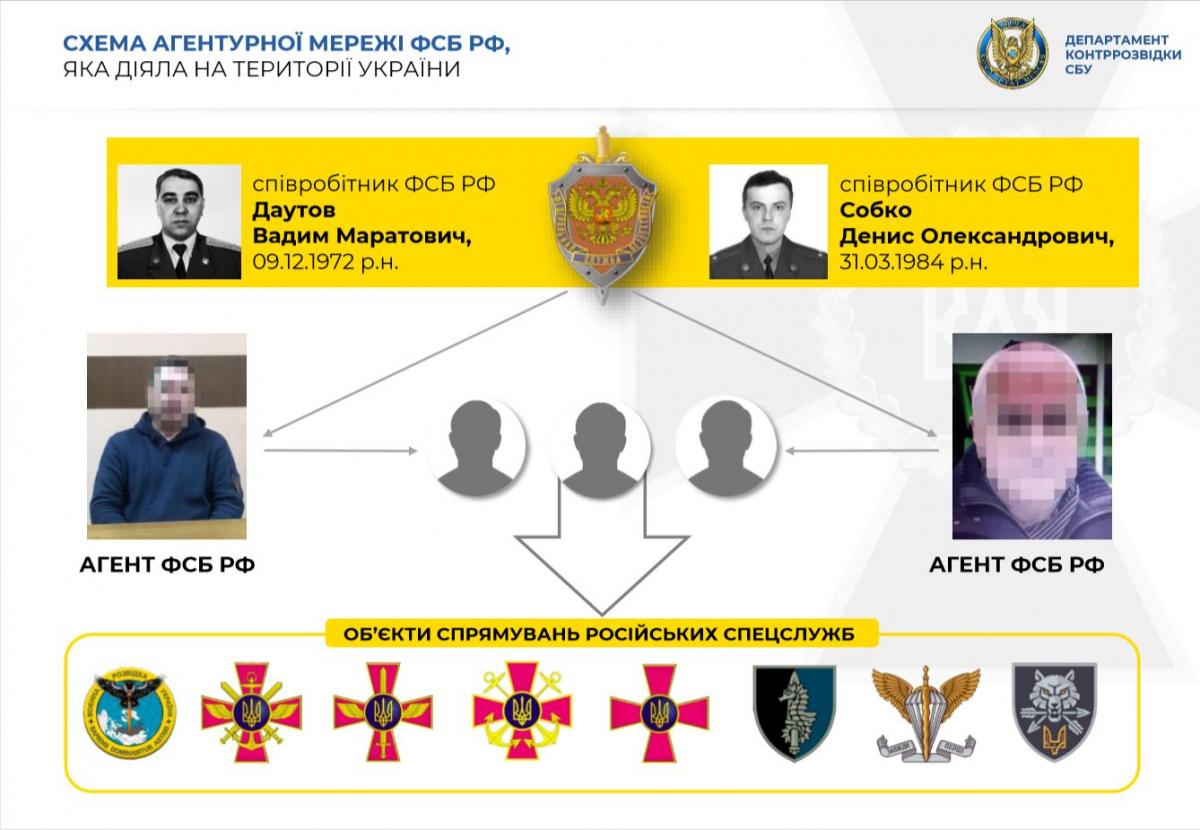
The SBU went as far as revealing the names of the assets' handlers in Russia – FSB officers Vadim Daut and Denis Sobko.
The network had been operating in Kyiv, Odesa, Mykolaiv, Zhytomyr, and Chernihiv regions of Ukraine.
Security officials say the Ukrainian turncoats have been tasked with creating conditions for subversive groups to illegally cross into Ukraine's Mykolaiv region from the temporarily occupied territories. Also, the assets were told to train attack groups.
Among the enemy targets were Ukraine Air Force warplanes stationed at the Kulbakino Airfield.
Besides, the investigators say, the Russian agents have been gathering intelligence on movement, personnel, and activity of Ukraine's military intelligence, Special Operations Force, Navy HQ, and the 73rd Marine Center for Special Operations, as well as their cooperation with international partners.

The assets were also trying to recruit senior military officials, the report says, adding that one of their tasks was to abduct and transfer to Russia one of the former commanders of the Special Operations Force – for a monetary reward of US$100,000.
Read alsoExposed: Russia's military intel behind "destructive" Telegram channels prominent in UkraineDuring raids, security officials seized an arsenal of weapons and ammo.
Criminal cases have been opened on treason, terrorism, and illegal arms handling charges.
At the same time, FSB officers involved are targeted in an espionage case.

