
The journalist started his search from the website вштабе.рф, a large photo gallery of pro-Russian memes and “demotivator” graphics. Most of these crude caricatures ridicule US, Western, and Ukrainian leaders, whilst portraying Vladimir Putin as strong and heroic, according to GlobalVoicesOnline.
“The site gives no credit or attribution for its design, and offers no indication as to who might be behind it,” Alexander wrote, “Intrigued by this anonymity, I used Maltego open-source intelligence software to gather any publicly-available information that might provide clues.”

The use of Maltego revealed that the site was running Google Analytics, a commonly used online analytics tool that allows a website owner to gather statistics on visitors, such as their country, browser, and operating system. For convenience, multiple sites can be managed under a single Google analytics account. This account has a unique identifying “UA” number, contained in the Analytics script embedded in the website's code.
Several free services have sprung up that allow easy reverse searching of Google Analytics ID numbers, one of the most popular being sameID.net.
Viewing the website's source code gave Alexander the all-important Google Analytics ID number. When he performed a broader search on it, the results were surprising—it was linked to no less than seven other websites.
These included whoswho.com.ua (archive), apparently aimed at collating compromising information on Ukrainian officials, whilst purporting to be a Ukrainian project; Zanogo.com (archive), another repository of memes, many anti-Western; and yapatriot.ru (archive), which appears to be an attempt to discredit Russian opposition figures. Another of the websites using the same Analytics account was syriainform.com (archive), a site seemingly promoting an anti-US and pro-Assad slant on events in Syria.
Whilst investigating the network of sites tied to one account, the journalist discovered that one, news-region.ru, had also been linked to a second Analytics account, which, in turn, was associated with a further cluster of nineteen pro-Kremlin websites. Subsequent examinations of these webpages revealed three more Analytics accounts, with additional sites connected to them. Below is a network diagram of the relationships Alexander has established to date.

“Besides Google Analytics, the websites had some other common traits: shared use of Yandex Metrika, Yandex Verification, and a Nginx server—all Russian-made tools—characterized the sites in the network. It became clear that I was most likely looking at a large, well-organised online information campaign. But whilst the Google Analytics code demonstrated shared involvement in and management of the websites, it couldn't tell me who was behind them,” said the journalist.
Having dug through publicly available information. Lawrence revealed a common e-mail address terder.n@gmail.com. It was associated not only with the majority of already identified sites, but also with a new group of websites, apparently still under construction. Their titles suggested themes similar to the existing network: either overt pro-Russian polemic, or more subtle disinformation under the guise of legitimate Ukrainian journalism.
They included antiliberalism.com, dnepropetrovsknews.com, maidanreload.com.
It took the journalist less than a minute of searching to link the e-mail address to a real identity. A group on Russian social networking site VKontakte [archive] lists it as belonging to one Nikita Podgorny.
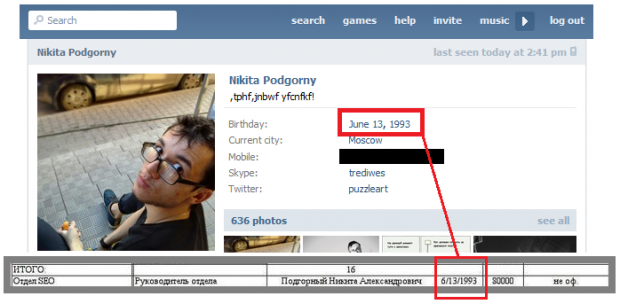
Most notably, Podgorny is listed in the leaked employee list of St. Petersburg's Internet Research Agency, the pro-Kremlin troll farm featured in numerous newsreports and investigations, including RuNet Echo's own reports.
Podgorny's date of birth, given on his public VK profile, is an exact match for that shown in the leaked document.

